Our Security Practices
At TrueEngage, the security of our platform, data, and customers is our highest priority. We implement a multi-layered security strategy aligned with international best practices, including ISO/IEC 27001:2022.
This article outlines the key technical and organizational security controls we have implemented to safeguard your data and ensure platform reliability.
1. Infrastructure and Data Center Security
Our platform is hosted entirely on Microsoft Azure, leveraging its industry-leading security, compliance, and resilience features.
-
Hosting Region: Primary infrastructure is deployed in Azure West Europe, ensuring all data processing remains within the European Union by default to comply with EU data protection requirements.
US-based storage options are available upon customer request. -
Environment:
-
Azure Kubernetes Service (AKS) for container orchestration and automated scaling
-
Azure Database for PostgreSQL (managed)
-
Managed Redis for caching and session management
-
Azure Blob Storage for unstructured data
-
Azure Queue Storage for asynchronous message handling
-
-
Physical and Environmental Safeguards: Azure’s data centers maintain advanced physical security, power redundancy, and disaster-resistant infrastructure.
To enhance global performance and resilience, Edgio CDN is used for secure and accelerated content delivery.
2. Network and Perimeter Security
We implement robust controls to protect against unauthorized access and network-based threats.
-
Network Segmentation: All production services are isolated within private Azure VNets.
-
Ingress Protection: Azure Load Balancer routes inbound traffic, providing DDoS protection and SSL/TLS termination.
-
Firewall and NSG Rules: Strict Network Security Group (NSG) configurations and IP whitelisting (e.g., SSH access restricted to office IPs).
-
Encryption in Transit: TLS 1.2+ enforced for all communications.
-
Edge Security: Azure CDN and Web Application Firewall (WAF) protect against external threats.
3. Data Security and Privacy Controls
We enforce strict measures to ensure all customer data remains secure and isolated.
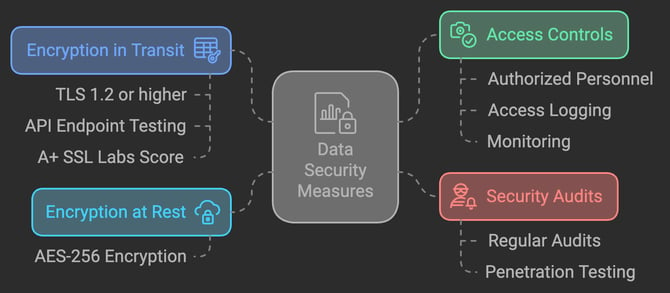
Data Security Measures
-
Encryption in Transit:
-
TLS 1.2 or higher
-
API endpoint testing
-
A+ SSL Labs score
-
-
Encryption at Rest:
-
AES-256 encryption on all storage systems
-
-
Access Controls:
-
Authorized personnel only
-
Comprehensive access logging
-
Continuous monitoring
-
-
Security Audits:
-
Regular audits and reviews
-
Annual penetration testing by certified providers
-
Additional Safeguards
-
Data Segregation: Tenant data is logically separated via scoped APIs and access policies.
-
Data Residency: Data remains within EU boundaries unless explicitly requested otherwise.
-
Backups: Daily automated backups with Point-in-Time Recovery (PITR) and regular snapshotting of persistent volumes (Velero).
4. Platform Architecture and Data Flow
Our platform is designed for resilience, scalability, and data security through modular, containerized microservices hosted in Azure.
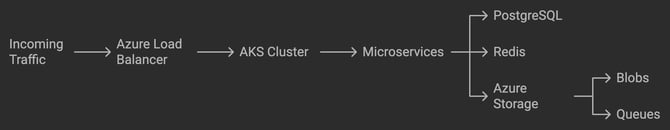
Data Flow Overview:
-
Incoming traffic passes through the Azure Load Balancer for SSL/TLS termination and DDoS protection.
-
Requests enter the AKS Cluster, where containerized microservices handle logic and routing.
-
Microservices interact securely with:
-
PostgreSQL (transactional database)
-
Redis (in-memory caching and session management)
-
Azure Storage (file management)
-
Azure Queues (asynchronous message processing)
-
All components communicate over encrypted channels within private Azure VNets to ensure confidentiality and integrity.
5. Access Control and Identity Management
Access to production environments is tightly governed by role-based policies and continuous monitoring.
-
Multi-Factor Authentication (MFA): Enforced for all internal and production system access.
-
Role-Based Access Control (RBAC): Applied across applications, infrastructure, and CI/CD pipelines.
-
Least Privilege Principle: Access granted only when required and regularly reviewed.
-
Comprehensive Logging: All access and administrative actions are logged and monitored.
6. Secure Development and Deployment
Security is integrated into every stage of our Secure Software Development Lifecycle (Secure SDLC).
-
Code Security: Mandatory code reviews and automated static analysis.
-
Continuous Integration/Continuous Deployment (CI/CD): Automated pipelines ensure consistent, tested deployments.
-
Vulnerability Management: Regular security updates and proactive patch management.
-
Application Policies: Enforce fine-grained access controls within application logic.
7. Monitoring, Logging, and Incident Response
Comprehensive monitoring and analytics ensure real-time visibility and rapid response to potential threats.
-
SIEM and Threat Detection:
-
Wazuh for centralized log aggregation and security monitoring.
-
Azure Defender and endpoint protection across all systems.
-
-
Performance Monitoring:
-
New Relic provides real-time visibility into application and infrastructure health.
-
Features include advanced alerting, anomaly detection, and transaction tracing.
-
-
Audit Logs: Secure, immutable, and continuously reviewed for suspicious activities.
-
Incident Response: Formalized procedures for identification, escalation, and resolution of incidents.
8. Backup, Disaster Recovery, and Business Continuity
TrueEngage maintains comprehensive recovery and continuity measures to minimize disruption and data loss.
-
Daily Backups: Automated backups with geographically redundant storage.
-
Point-in-Time Recovery: Enables rapid restoration of databases to any previous state.
-
Disaster Recovery Plan (DRP): Tested and reviewed annually.
-
Business Continuity Plan (BCP): Ensures critical operations remain functional during major incidents.
9. Ongoing Security Assurance
We maintain continuous improvement of our security posture through:
-
Regular security audits and compliance reviews
-
Continuous monitoring and proactive threat detection
-
Employee security awareness and training
-
Adherence to ISO/IEC 27001:2022 controls and objectives
Summary
TrueEngage’s architecture and security practices are built around defense in depth, regulatory compliance, and resilience.
Through Azure’s secure foundation, layered access controls, continuous monitoring, and rigorous testing, we ensure a secure, scalable, and compliant environment for all customers.